WARNING –> This is a long read, so I wrote most of the important stuff up top!
While the future of technology is usually exciting, it’s also important to temper so much hype with some healthy reality and practical, thoughtful and intentional consideration. Arguably, out of all the recent hype, out of all the recent advances in tech, the Internet of Things, from both consumer (IoT) and industrial (IIoT) perspectives, has generated a great amount. I often answer questions about IoT so I made some time to do a brain dump here, both for personal and professional reflection and to clear out some old ideas and welcome some new, to clarify my own perspective and to share information that’s as balanced as possible about this polarizing buzzword/acronym, IoT.  First, the consumer perspective. Generally speaking, when someone says ‘IoT’ they’re talking about the consumer side of that coin, so let’s talk about that first.
First, the consumer perspective. Generally speaking, when someone says ‘IoT’ they’re talking about the consumer side of that coin, so let’s talk about that first.
Consumer Internet of Things (IoT – The Dark Side)
First off, it’s important to state how these early consumer IoT devices are not good choices for kids. Anyone can read for themselves about the risks of giving Internet-connected devices to children. Some parents will somehow miss those articles by the NYT, BoingBoing, and others and continue to buy those gadgets for their kids in ratios directly proportional to their lack of awareness and general technical fluency. Those devices are so insecure that entire countries have (wisely) banned them. The experts have written extensively about how unprepared the world is in general to have IoT devices in their homes, even as grown-ups. We can read about how they’re being used in domestic partnerships to terrorize women and about IoT-powered botnets here, the perils of “smart jewelry” there, and how millions of unsuspecting and uninformed people are adding millions of unsecured devices into the wild and how this makes things, well, unpredictable at best. Even the wearable tech many people wear on their wrist is sharing deeply personal information that is being used without their consent.
The truth is: using the technology we already have (mobile phones, laptops, tablets, etc) in safe and secure ways is still a challenge for a vast majority of us.
While we like to think we’re ready for every next-new-thing, ready to buy this or that, the truth is adding devices that provide even deeper penetration into our habits, preferences and personal information (wearables, smart home devices, etc) isn’t a great idea because the information we unwillingly share will be used in ways we likely hadn’t considered, such as tracking us to monitor how often we speed (to raise our car insurance premiums) or how sedentary we are (to raise our health insurance premiums and change product offerings), and worse violations of our privacy by taking advantage of manipulative apps and opt-in services that are intentionally misleading to consumers.
While this has only just begun and most people are unaware of it, in the coming years it will be too late for them to do anything about it as news disseminates into the mainstream.
Taking advantage of people is easy. Most of us are distracted by technology to epidemic proportions.
While these new technologies always enter our lives with the promise of adding value, giving us time back to spend being present for things that really matter, the data shows the consumer side of IoT has little value to add outside of a convenience here and there rather than solving our presence problems, meeting a real need, or offering much of anything that’s practical. Not yet, anyway.
We rarely ask ourselves, “Why do I need this?” The more uninformed we are, the less we seem to consider the privacy perspective or why that matters.
Smart Homes?
Connected devices exist and continue to grow in numbers, from televisions to toasters to refrigerators, cars, houses and more. Most of us in the technology industry don’t think of this as IoT as much as just the internet, as it is, growing and assimilating everything.
So, with that in mind, what’s good about it? What devices have practical value through solving a genuine need and not just less valuable layers of convenience?
Nest is cool. I like saving energy without having to do anything. This is one area where so-called smart devices are worthwhile in the consumer space. It detects the weather and adjusts the temperature based on some basic configurations. I like monthly reports on what I’m spending on heating and cooling, based on the time of year. I like the utility of it, that I can throw small, unobtrusive cameras up that keeps a record of uninvited people coming and going around the house.
I’m not sold on making my home full-on “smart”, yet, though, and the limited smart devices that exist are present on their own network, separate from the network the kids use for their activities, which is also separate from the network my wife and I use for our work.
Network segregation is essential for any devices using any STUN-like technology (which most “smart-home” products employ) in order to keep others’ from easily prying into places they’re not welcome.
My pals who praise the presence of voice-recognition appliances in their homes to make them “smart”, like Alexa and Google Home, still cannot convince me these solve genuine needs. They don’t strike me as even practical on a level that makes any sense, especially being aware that the companies who manufacture them are getting a way better deal, listening into the lives and habits of all those who are willingly to put these sanctioned surveillance devices in their homes.
There’s already enough proof for concern. This isn’t the last we will hear of this. Not even close.
Industrial Internet of Things (IIoT – The Bright Side) 
This is where I’m going to get into the details. This is the market segment that is driving and solving many practical problems, even initial challenges first uncovered in the early deployments, from power obstacles being solved by LoRa technology, to better visibility into what’s been deployed, and the administration, automation and security of massive IIoT deployments.
These are all equal challenges on the consumer side, too, and so as we get better at solving things at scale, the cost of these solutions will come down as the reliability, friendliness and accessibility continue to grow, albeit at a slower pace than in industrial applications of IoT.
Regarding the industrial IoT or IIoT, upon close consideration of the current level of available infrastructure and supporting technologies, well, they are not capable of supporting it in a sustainable way. Think of the Internet of Things as the Internet to come with next generation everything (meaning more than 802.xx (WiFi) standards, 3/4/5G/LTE/Ethernet backhaul architecture, IPv6, bandwidth and security practices) that can support it sustainably.
Like the evolution of so many things, The Internet, too, evolves moment-to-moment. Companies that are deploying massive IoT networks are doing so successfully by deploying along with it their own, supporting infrastructure that includes the technologies that can sustain it over the long-term.  This includes deployments for manufacturing, transportation, distribution, retail, etc.
This includes deployments for manufacturing, transportation, distribution, retail, etc.
In manufacturing, smart sensors are installed on manufacturing equipment to measure vibration, heat and more in order to pro-actively service these machines to save millions in maintenance costs.
Likewise in transportation contexts, sensors can measure things like RPMs, temperature, and more in the context of preventing failures before they happen.
For example, use of new technical standards for performance and security, such as Machine to Machine (M2M) protocols to communicate, trucks and their engines can communicate with each other and compare notes, so to speak, such as “I just rolled past 121,000 miles and my timing belt needs adjustment. How about you?”
Imagine how much time, money and labor this kind of information can save a supply chain enterprise like a trucking company. That’s useful.
In the warehouse, IIoT can achieve similar cost savings and better inventory management, barring that first organizations have to ensure the pains of solving the management challenges presented by adding this level of complexity into their operations.
Embedding sensors into inventory management workflows can help streamline operations but not without first throwing down some serious time and cheddar to establish sustainable network infrastructure, cyber resilience practices and overall fluency in the culture.
Retail faces similar challenges. Building awareness of and fluency with consumers is one thing. Building them into industrial cultures is every bit as challenging, if not more. Culture is always the biggest challenge any time a new technology is introduced into the wild. Managing machines is way easier than empowering the people who manage the machines. Shifting the way people think is a slow and tedious process, especially where getting them to embrace good practices is concerned. Otherwise, new technologies create more new problems than the old problems they were designed and deployed to solve.
The Numbers 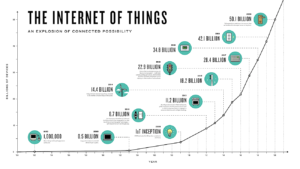
Here’s what that means in the context of the sheer number of devices being connected to it: According to average estimates, over 200 billion devices (mostly in industrial contexts) will be in use worldwide by the end of 2020, an exponential increase from previous estimates.
Truth is, no one really knows how many there will be but consensus is that it will be at least that many, likely more as these things tend to go. Many predict those numbers are conservative estimates.
Unprecedented opportunities present themselves in all of this. For example, instead of having conversations about response to issues, such as hardware failure, deep insight provided by machine-to-machine communication at the edge of decentralized networks, enables us to discuss concepts like prevention for the first time due to the improved utility, efficiency and safety delivered by new insights into the data gathered by the sheer numbers of connected sensors and smart devices.
However, there are inherent challenges that come along with such growth. These challenges within IoT are also new and, in some cases, unfamiliar, and without the right considerations can put a serious dent in the value this data delivers. As IoT becomes more real and present in our lives, the tech community is (sort of) getting prepared to deal with the challenges it will present.
Infrastructure and Addressable IP Space 
I say “sort of” because many in the tech community are unaware of some of the key infrastructure considerations that need to be addressed before any such consumer and/or industrial IoT deployments take place in sustainable ways.
First among these considerations is this: as the number of IoT devices continue to grow, we are running out of IP addresses as most of us know them, still known as the original designers of TCP/IP defined them. An IP address is a 32-bit number and this system, named Internet Protocol Version 4 (IPv4), is still in use today. It looks like this: xxx.xxx.xxx.xxx or 173.194.68.102.
Your home network likely uses something that looks like this: 192.168.1.xxx where the ‘xxx’ is a number between 1 and 254. However, due to the astounding growth of the internet and the resulting depletion of that addressable number space, a new addressing system (IPv6) that uses 128 bits for the address, was developed quite awhile back (RFC 1883) in order to be able to scale in pace with demand for IP addresses.
Although IP addresses are stored as binary numbers, they are usually displayed in human-readable notations, such as 208.77.188.166 (for IPv4), and xxxx:xxx:x:xxxx:xxxx:xxxx:xxx::x (just an example, for IPv6). The role of the IP address has been characterized as follows: “A name indicates what we seek. An address indicates where it is. A route indicates how to get there.”
The idea of having a subnet with 1.8446744074 x 1019 available addresses and only using two of them – and knowing that you will never, ever need more than two of them – seems mind-bogglingly wasteful. And it is wasteful. But the IPv6 address space assigned to most networks is so vast, you can afford a shocking level of waste in exchange for consistency, simplicity, scale, and efficiency. If you have a /32 prefix, you can have 4.3 billion /64 subnets – as many subnets as there are addresses in the entirety of IPv4.
Identity and Access (another way of talking about security) 
Identifying devices within a network is key to securing IoT ecosystems and preventing the infiltration of intruders. In current solutions, device authentication and authorization is mostly carried out through centralized cloud-based servers, which is perfectly viable in small-scale IoT networks where dozens of nodes are involved.
As ecosystems start to grow and thousands and millions of sensors and gadgets enter the fray, authentication can become a bottleneck, especially if the network loses internet connection for any amount of time.
Understanding the notion of scale is essential in defining effective security strategies and realistic mechanisms to control bazillions of devices. Current solutions and thinking rely on internet connections tough on batteries and overwhelming to the networks most IoT systems rely on and fail completely when a lack of resiliency causes their connectivity to go down.
This is why it’s true that there are a lot of challenges to solve because the old model of computing doesn’t hold up where under this new paradigm.
The solution is peer-based functionality at the edge, between devices themselves, via machine-to-machine (M2M) protocols, making it easier to scale. Displacing authentication/authorization activities from centralized architectures to the devices themselves, without requiring internet access, networks perform faster and more securely, too.
Networks can be secured through policies stored in individual devices. Policies can be distributed from the cloud or delivered through Bluetooth or directly-connected media posts, like USB sticks. Strong hash chaining techniques ensure the safe transmission of these.
Wireless and Mobility: Power and Signal Solutions 
At its core, IoT is just another way to talk about the internet. It is the extension of worldwide web connectivity from our computers to devices and sensors that surround us and, self-evidently, that connectivity has to be wireless, especially in the personal area network, i.e. the ensemble of wearable, portable and implanted devices we will carry around with us.
Many IoT devices rely on radio frequency (RF) technology such as Bluetooth, ZigBee and Wi-Fi for communications. Otherwise known as far-field transmission, RF is great when communicating over long distances, but becomes problematic when applied to short-range, isolated IoT ecosystems, due to conflicting with each other, making management of thousands, tens of thousands, etc. more difficult to manage in predictable and friendly ways.
The administrative tools that provide visibility into these large, industrial deployments are still in their infancy. For example, RF-based devices can shut each other down due to interference, a situation that is growing exponentially as device counts move into the billions.
Think of it like a stew that we’ve put too many ingredients into. There’s hardly any liquid left. It’s become saturated. Same with RF. The channels or frequencies are full, which means the soup is saturated. This causes interference.
The FCC will have no choice but to open up additional bandwidth such as 5GHz for 802.xx before device counts rise into trillions into to solve for this.
Power consumption continues to be the bane of these systems, too, as many are powered by batteries and are in use in environments where physically accessing them to change a battery, for example, is not practical. Power technology still seems antiquated and will need a renaissance prior to IIoT being more resistant to faults and failures in the systems.  Near Field Magnetic Induction (NFMI), for example, is a great alternative for RF. NFMI uses magnetic fields to transfer data wirelessly between two points over Machine to Machine (M2M) protocols. Its main strength is its attenuation, which means the signals it transmits decay exponentially faster than RF signals do, which solves the interference challenges and helps minimize some of the cybersecurity issues that plague more persistent technologies, such as Bluetooth, which is a malicious hacker’s best friend.
Near Field Magnetic Induction (NFMI), for example, is a great alternative for RF. NFMI uses magnetic fields to transfer data wirelessly between two points over Machine to Machine (M2M) protocols. Its main strength is its attenuation, which means the signals it transmits decay exponentially faster than RF signals do, which solves the interference challenges and helps minimize some of the cybersecurity issues that plague more persistent technologies, such as Bluetooth, which is a malicious hacker’s best friend.
NFMI is based on the same principle as Near Field Communication (NFC), which is found in all new-generation smartphones, but it extends the reading distance from 1-4 inches up to 9 feet and offers a 400 Kbps data transfer rate. NFMI has also been proven, as it has already been implemented in hearing aids, pacemakers and mission critical systems and communications technologies for more than a decade.
Administration and Visibility 
As the number of IoT devices deployed increases, administrating them can quickly turn into a huge challenge. In order to make the best use of the increased utility provided by the millions of smart meters, parking and lighting sensors, traffic controls, crowd movement detection sensors and many other gadgets that are scattered across smart homes and cities, you need to be able to efficiently control their traffic and functionality.
Administration, integration and connectivity should be as simple as possible and require the least amount of human interaction and/or intervention.
The machines are making us slaves right now, having to guide so many activities that could be automated. Imagine the moments of our lives we will never get back configuring and testing what will seem so archaic in just a few years time. Very soon, we will be able to see and do more, from an administration perspective, with exponentially less effort.
Change
The many management and infrastructure transformations involved with the Internet of Things will have both technical and cultural implications. For example, such a robust upgrade in infrastructure will also set the stage for Mixed Reality (AR and VR) applications and platforms that are emerging in parallel and also require more bandwidth and IP space.
Culturally and collectively, these will impact how humans interact with machines to access, share and protect our information. It’s also important to keep in mind, where new technologies are concerned, the timelines we read about are most often greatly exaggerated. It will take some time for things like Machine Learning, Augmented Reality (AR), Virtual Reality (VR), Mixed Reality (MR) and Artificial Intelligence (AI) to take their place in our lives like we imagine.
While these potentials are exciting, what’s arguably more exciting is how they might work together to help real people make greater connections with each and the real world around us.